JumpCloud’s automated patch management helps you keep your managed macOS devices and apps secure and updated. As an IT Admin with Manager role permissions or higher, you can manage and enforce when major OS upgrades and minor update patches are available and applied to your devices. You can also configure how much flexibility your users have in delaying or canceling the update:
- Major OS upgrades – Control when users install the latest available OS upgrade. You might want to test a new OS version on a small number of devices before you roll out a new upgrade to your entire company. You can defer an upgrade for 90 days after its release. You can specify a major upgrade installation per operating system, which gets installed on target devices within 24 hours of applying the policy. Enforced major upgrades utilize Mobile Device Management (MDM) software install commands and do not require end user interaction or Admin permissions.
- Minor update patches – Specify when minor updates become available to a device and control how long users can defer the update. If you choose to force minor updates to your users’ devices, you must set a deadline for minor updates. As that deadline approaches, automatic reminders appear more frequently and eventually users cannot dismiss them. If the deadline expires, the policy then forces a minor OS update to be automatically downloaded and installed using MDM software install commands.
You can customize user reminders for minor updates and preview the reminder before it is displayed to users. If you uploaded your logo, it also appears in the reminder. OS patch policies work on macOS Big Sur 11 and later.
JumpCloud also provides a universal browser patch policy that keeps Google Chrome up to date for macOS, Windows, and Linux. See Create a Universal Browser Patch Policy.
You can save time by using JumpCloud’s default patch policies and policy groups that are preconfigured and ready to use. See Configure Default Patch Policies and Policy Groups.
Contact your Account Manager if you’re interested in adding OS and browser patch management to your package or to learn more about the solution. Pricing for patch management is located at https://jumpcloud.com/pricing.
Creating Default Patch Policies and Policy Groups
If your organization has not yet configured any macOS, Windows, or Linux patch management policies or policy groups, you can save time by loading a set of default policies and policy groups. These patch policies and groups can save you time by enforcing security patches on a large number of managed devices.
A policy group helps you quickly and efficiently roll out preconfigured policies using deployment rings. Deployment rings are configured with sane defaults. The deployment ring names match these policy group names, and control how and when an update is applied:
- Vanguard – Deploy automated upgrades inside your IT Department.
- Early Adoption – Deploy automated upgrades to early adopters outside of IT.
- General Adoption – Deploy automated upgrades to general users in your company.
- Late Adoption – Deploy automated upgrades to remaining users in your company.

To create default patch policies and policy groups:
- Log in to the JumpCloud Admin Portal.
- Go to DEVICE MANAGEMENT > Policy Management.
- Select Patch Management, then select the OS tab.
- If you haven’t yet configured a patch policy or patch policy group, click Load Default Policies & Policy Groups to create four out-of-the-box default policy groups. Each policy group contains three preconfigured deployment ring policies that are automatically bound to the group.

- Review the preconfigured settings for the macOS default policies:
- Defer Update Releases – The number of days to defer the availability of future minor OS updates. If you set the deferral length to be greater than the number of days since a minor update was released, this update will not be available. Any minor release older than 90 days will not be affected. Deferral Length in Days specifies how many days to defer a minor OS update after it’s released.
- Enforce Automatic Updates – The number of days that users have to install minor OS updates after they are available. The Installation Deadline in Days will apply to any minor OS updates available on a device at the time of policy application. If minor updates are not installed at the end of the deadline, JumpCloud forces the update via an MDM command. Valid values are 0-90 days, and the default is 30 days.
When the delay periods and the deadline that you set in Step 5 expire, the policy forces a minor OS update to be automatically downloaded and installed as soon as the user's device comes online. This action occurs for updates to macOS 11, macOS 12, and macOS 13. If something unexpected happens and the minor update could not be installed, JumpCloud will try again every 24 hours.
| Deployment Policy Ring | Deferral Length in Days | Installation Deadline in Days |
|---|---|---|
| macOS Vanguard | N/A | 3 days |
| macOS Early Adopter | 7 days | 7 days |
| macOS Early Adopter | 15 days | 10 days |
| macOS Late Adopter | 30 days | 10 days |
When selecting a policy, the Deferral Length in Days setting for minor update releases will apply to any future minor updates.
- You can configure additional settings that are not preconfigured in the default policies:
- Defer Upgrade Releases – Delay users from installing the latest available OS upgrade. For Deferral Length in Days, enter the number of days you want to defer a major OS upgrade after it’s released. You can defer an upgrade for 90 days after its release. After that, this setting only applies to the next major OS upgrade. The minimum value is 1 day and the maximum is 90 days. The default is 30 days. The macOS Ventura release has been available for more than 90 days, so this setting would apply to Apple’s next major software release (macOS 14).
- Defer Non-OS Updates – Delay users from installing non-OS updates. Examples of non-OS updates are a Safari update or an Xcode Command Line Tools update. For Deferral Length in Days, enter the number of days to defer non-OS updates after they are released. The minimum value is 1 day and the maximum is 90 days. The default is 30 days.
- (Optional) Review your default policy groups and policies. The policies are automatically bound to the appropriate group.

For example, the Vanguard Ring Policy Group automatically contains these three preconfigured deployment ring policies:- Linux (Ubuntu) Vanguard Ring
- MacOS Vanguard Ring
- Windows Vanguard Ring
If you already created default policies and groups, and later you create additional default policies or policy groups, an error does not appear. Instead, the existing default policies and policy groups will be used.
- (Optional) Select the policy you just created and select the Device Groups tab. Select one or more device groups where you’ll apply this policy. For device groups with multiple OS member types, the policy is applied only to the supported OS.
- (Optional) Select Devices. Select one or more devices where you’ll apply this policy.
For this policy to take effect, you must specify a device or a device group in Step 8 or Step 9.
- Click save.
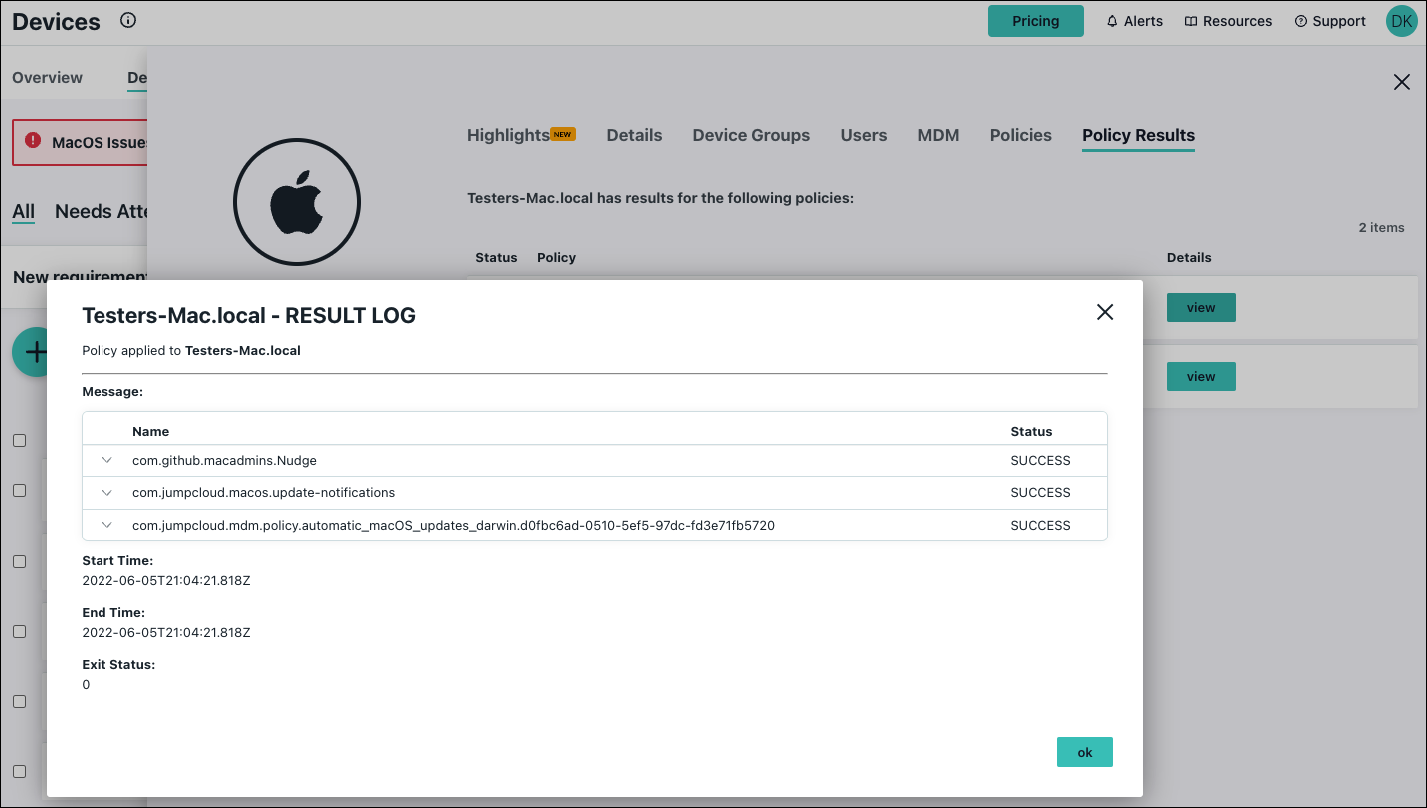
- After the policy runs, you can view detailed results for a specific device:
- Go to DEVICE MANAGEMENT > Devices.
- Select the Devices tab, then select the device.
- Select Policy Results, then click view to see more details. An Exit Code of 0 indicates that the policy ran successfully.
- To delete a patch policy, select the checkbox next to the policy and click delete. The policy is removed from the OS Patch Management list.
Creating an Automatic MacOS Updates Policy
You must have Manager role permissions or higher to create and enforce a patch management policy.
To create an Automatic MacOS Updates policy:
- Log in to the JumpCloud Admin Portal: https://console.jumpcloud.com/login.
- Go to DEVICE MANAGEMENT > Policy Management.
- Select Patch Management, then select the OS tab. Only OS patch policies appear in this tab.
- To create a new, custom Automatic MacOS Updates Policy, click (+), then choose macOS.

If you don't see the + when the OS tab is selected, click Load Default Policies & Policy Groups. See Creating Default Patch Policies and Policy Groups above.
- (Optional) On the New Policy panel, enter a new name for the policy or keep the default. Policy names must be unique.
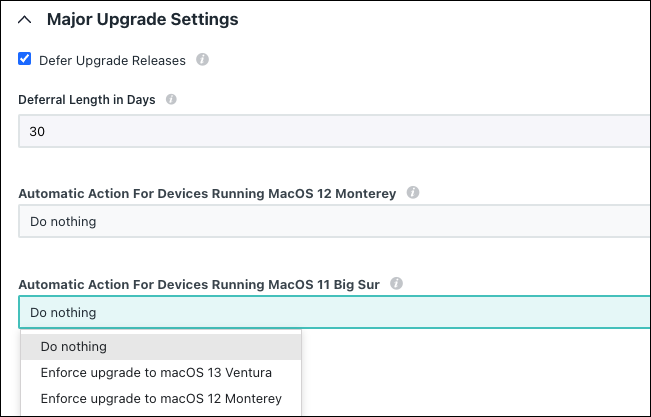
- Under Major Upgrade Settings, configure any combination of these settings:
- Select Defer Upgrade Releases to delay users from installing the latest available OS upgrade. You can defer an upgrade for 90 days after its release. After that, this setting only applies to the next major OS upgrade.
- For Deferral Length in Days, enter the number of days you want to defer a major OS upgrade after it’s released. The minimum value is 1 day and the maximum is 90 days. The default is 30 days.
- Choose one or both of these options if you want to automatically upgrade to a specified OS version within 24 hours:
- Automatic Action for Devices Running MacOS 12 Monterey:
- Do nothing – Devices currently running macOS 12 Monterey will not be upgraded.
- Upgrade to macOS 13 Ventura – Devices with this policy applied to them that are currently running macOS 12 Monterey will be upgraded to macOS 13 Ventura.
- Automatic Action for Devices Running MacOS 11 Big Sur:
- Do nothing – Devices currently running macOS 11 Big Sur will not be upgraded.
- Upgrade to macOS 12 Monterey – Devices with this policy applied to them that are currently running macOS 11 Big Sur will be upgraded to macOS 12 Monterey.
- Upgrade to macOS 13 Ventura – Devices with this policy applied to them that are currently running macOS 11 Big Sur will be upgraded to macOS 13 Ventura.
- Automatic Action for Devices Running MacOS 12 Monterey:
- Select Defer Upgrade Releases to delay users from installing the latest available OS upgrade. You can defer an upgrade for 90 days after its release. After that, this setting only applies to the next major OS upgrade.
If the policy is configured to upgrade macOS 12 to 13 and mac OS 11 to 12, users running macOS 11 will be subjected to two major upgrades. The end result would be users currently running macOS 11 will eventually be upgraded to macOS 13.
- Under Minor Update Settings, configure any combination of these fields:
- Select Defer Update Releases to delay users from installing the latest available minor update. You can defer an update for 90 days after its release.
- For Deferral Length in Days, enter the number of days you want to defer a minor update after it’s released. The minimum value is 1 day and the maximum is 90 days. The default is 30 days.
- Select Enforce Automatic Updates to prompt users to install available minor updates based on the current OS. If users don’t install updates before the deadline, those updates will be automatically installed.
- For Installation Deadline in Days enter the number of days users have to install a minor update after it’s available. If updates aren’t installed before the deadline expires, update commands are sent daily until the device is updated. The minimum value is 0 days and the maximum is 90 days. The default is 30 days.
- Entering an Installation Deadline in Days that is equal or less than the number of days since the update was released (refer to the Release Trains table on the Policy Management > Patch Management tab) will trigger an immediate update on unpatched devices.
- Select Defer Non-OS Updates to delay users from installing non-OS updates. Examples of non-OS updates are a Safari update or an Xcode Command Line Tools update. You can defer updates for 90 days after their release.
- For Deferral Length in Days, enter the number of days to defer non-OS updates after they are released. The minimum value is 1 day and the maximum is 90 days. The default is 30 days.

- For Deferral Length in Days, enter the number of days to defer non-OS updates after they are released. The minimum value is 1 day and the maximum is 90 days. The default is 30 days.
- Select Defer Update Releases to delay users from installing the latest available minor update. You can defer an update for 90 days after its release.
If a major OS upgrade and a minor version update are available at the same time, a major OS upgrade takes precedence over a minor update.
- (Optional) Under Notification Settings, you can create a personalized message for your users when a minor update is available. You can choose to display custom notifications for minor updates to your users.
- Select Enable Custom Minor Update Notifications to send personalized notifications to your users about minor updates. If you do not select this, users will not receive notifications about new updates and will not be notified of installation deadlines. Instead, users will see native notifications about updates from Apple.
- For Update Notification Message, enter a custom message that your users see when updating. The maximum length for the message is 75 characters.
- To add your company’s logo to the notification, go to Settings and select the Organization Profile tab.
- Under Customize Logo, click Choose a File and upload your PNG or JPG logo file. A transparent or white background is required.
- Click Save. If you don’t upload a logo, the JumpCloud logo is used by default..
- Select a Notification Preview type and view how your logo and message will appear. You can choose to display custom notifications for minor updates to your users.
- Latest Update – The device is running the most recent macOS version. Users are prompted to click Update Device to install the latest minor version update for the current major OS.
- Minor Update – The device is not running the most recent major macOS version, but has a minor update available. Users are prompted to click Update Device to install the update.

If you enable notifications without inputting or selecting Installation Deadline Days in the previous step (7b), this defaults to a 0 day grace period which will force immediate updates on devices.
To prevent this, either:
- Increase the Installation Deadline Days in step 7b.
- Or disable both Enforce Automatic Updates (7b) and Custom Minor Update Notifications (8a).

- Click save.

Custom notifications are not available for major upgrades. If a device has a major macOS upgrade available to install, users with this policy applied to their devices are automatically upgraded via MDM commands. Users will see only the notification above that the upgrade is scheduled.
- Verify that the logo you uploaded appears correctly in the policy:
- Go to DEVICE MANAGEMENT > Policy Management.
- Select Patch Management, then select the OS tab.
- Select a new or existing policy that will have the custom reminder.
- In the policy’s Details tab, click Customization Settings. The logo that you uploaded in Step 8b appears here.
- (Optional) Select the policy you just created and select Device Groups. Select one or more device groups where you’ll apply this policy. For device groups with multiple OS member types, the policy is applied only to the supported OS.
- (Optional) Select Devices. Select one or more devices where you’ll apply this policy.
For this policy to take effect, you must specify a device or a device group in Step 11 or Step 12.
- Click save. The configured policy appears in the OS tab.
You can also create patch policies for Windows and Linux. See Create a Windows Patch Policy and Create a Linux Patch Policy.
Understanding MacOS Alerts
End user notifications will prompt users for minor updates when Enforce Automatic Updates option is enabled by the Admin. If Enforce Automatic Updates isn't enabled, users won't see the custom notification to update.
The alerts from JumpCloud begin once the device detects that it has an update available. Every five hours–twice per average working day–the alert window will launch and prompt the user to update the operating system.
When less than 72 hours remain in the deadline, the alert will increase in frequency from twice per working day to 6 times per working day, every 100 minutes. When less than 24 hours remain in the deadline, the alert will increase in frequency again from every 100 minutes to every 10 minutes.
When the deadline has elapsed, and the system is still not updated, the alerts will continue every 10 minutes, but the window can no longer be closed, will re-center on the screen every 10 minutes, and you cannot quit the app from the UI. If the user discovers the process and terminates it through the command line, it will regenerate.
Alerting Behavior Differences When Major OS Updates Are Available
There are alerting differences for the notifications presented to end users via this policy based on the major OS version a device is running.
- Update Notification When Running the Latest MacOS Version (MacOS Ventura)
When a device is running the latest macOS major OS version, the notification for a minor version update drives users to update their devices using the native flow via Apple’s System Preferences > Software Update.
The dialog in System Preferences that is opened by clicking Update Device will only show the available patches for the system. It shows new versions of the operating system that are already approved, and thus, eligible for update. Follow the steps onscreen to update your device.
When users are within a few days of the deadline for updating the device, they must click I understand to get the Close button to appear. As the IT Admin, you configure the deadline date in the Automatic MacOS Updates policy. After the deadline date passes, users must click Update Device.
- Update Notification When Major MacOS Update Are Available (MacOS Monterey or Big Sur)
When a device is not running the latest macOS major version, the notifications presented to end users provide additional information to drive them to update to the latest version of their supported operating system.
The dialog in System Preferences that opens when users click Update Device displays the macOS major version update, as well as instructions for More Info. This notification drives end users to click More Info to learn how to install the required update.
For example, a device that is not running the latest macOS version that is available for installation after clicking More Info can view details in Software Update in Apple’s System Preferences.
Removing a Patch Policy
To remove an existing patch policy:
- Log in to the JumpCloud Admin Portal: https://console.jumpcloud.com/login.
- Go to DEVICE MANAGEMENT > Policy Management.
- Select Patch Management, then select the OS tab.
- Select the policies you want to remove.
- Click Delete.
- Click continue.