User Groups in vCenter & JumpCloud LDAP
A common request from JumpCloud Administrators is to integrate JumpCloud's LDAP-as-a-Service with VMWare vCenter. JumpCloud's LDAP-as-a-Service is RFC2307 compliant, while vCenter currently supports RFC4519.
RFC4519 Schema:
- All users have an objectClass of inetOrgPerson.
- All groups have an objectClass of groupOfUniqueNames.
- All groups have a group membership attribute of uniqueMember.
- All users and group objects have entryUUID configured (The objects have a unique GUID and should not be changing)
This leads to Users working as expected for inetOrgPerson for JumpCloud. However, User Group functionality for groupOfNames with JumpCloud will not work. You can set up LDAP to JumpCloud with vCenter, but you will need to set up local vsphere.local User Groups and add JumpCloud LDAP Users as members.
This is an issue with the way that VMware has developed their OpenLDAP configuration by using the 4519 Schema instead of RFC2307. Please reach out to VMware to put in a feature request to support RFC2307, as this is not something JumpCloud can change or resolve with their LDAP Client in vCenter.
Configuring vCenter with JumpCloud LDAP
This configuration has only been verified for vCenter versions 6.0 through 6.7. This has not been tested or validated with vCenter 7.0 or newer.
VMware vCenter has several configuration types within its Identity Sources. To properly configure vCenter to use JumpCloud's LDAP, please configure the Identity Source via the following directions below:
You must configure JumpCloud's LDAP first before you can configure VMware vCenter. Please reference Use Cloud LDAP. The ORGID in the attributes below is your JumpCloud OrgID, found in either your LDAP settings in JumpCloud or via Settings in the JumpCloud Admin Portal.
- Log in to vCenter with your [email protected] credentials.
- Click on Menu at the top of the window.
- Navigate to Administration.
- On the left-hand navigation, expand Single-Sign-On and select Configuration.
- Navigate to Identity Sources tab in the right-hand pane.
- Create a new Identity Source by clicking Add Identity Source
- Select OpenLDAP as the Identity Source Type.
- Enter the following configurations into the listed attributes:
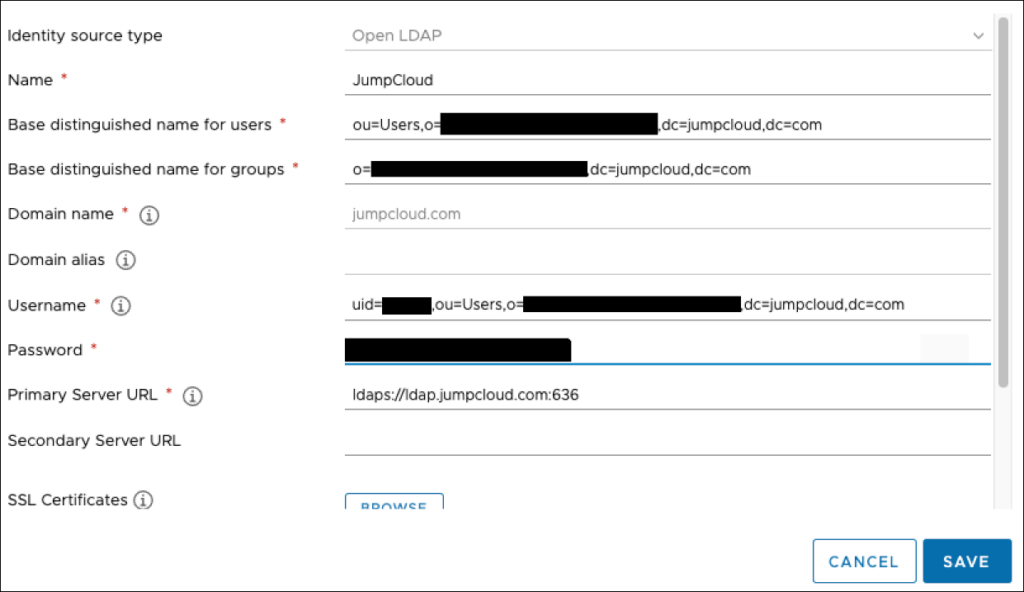
- Identity Source Name: JumpCloud LDAP
- Base Distinguished Name for Users: ou=Users,o=ORGID,dc=jumpcloud,dc=com
- Base Distinguished Name for Groups: o=ORGID,dc=jumpcloud,dc=com
- Domain Name: jumpcloud.com
- Username: uid=BINDDN_USERNAME,ou=Users,o=ORGID,dc=jumpcloud,dc=com
- This is the DN of the BindDN account you've created for JumpCloud LDAP. Please reference Use Cloud LDAP if you've not configured this already.
- Password: The password of the BinDN User within JumpCloud you've created.
- Primary Server URL: ldaps://ldap.jumpcloud.com:636
- Certificates (for LDAPS): Upload the .pem file from Connect to LDAP with TLS/SSL.
- Click Save.
- You now need to make the LDAP Identity Source with JumpCloud the default by doing the following:
- In the Identity Sources list, select the JumpCloud LDAP identity source radio button to the left hand side of the entry, then click Set As Default.
- You will be asked by vCenter to confirm, as you're changing the default domain from vsphere.local to JumpCloud's LDAP. Click OK.
- You should now see the following in your Identity Sources list. JumpCloud should be labeled as Default next to the OpenLdap entry.
Once you click Save, vCenter should be able to test the config and validate it successfully. If it errors out, check the configuration again to ensure that all of the attributes above are properly set. If it continues to error out, please reach out to VMware's support team to troubleshoot the Platform Service Controller.
Below is an example of a working configuration. We've edited out the OrgIDs and the Usernames from this example for security purposes.
Logging into vCenter with JumpCloud User Accounts
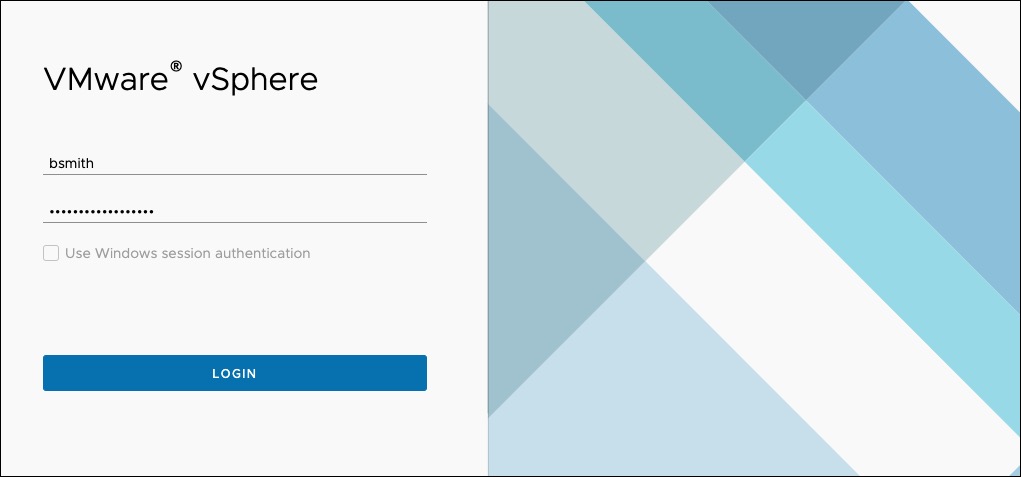
Now that you've set up vCenter with an Identity Source of JumpCloud via OpenLDAP, you will need to have users log in with their JumpCloud username and password. See the example.
The User in this example is Bob Smith. Bob's JumpCloud username is bsmith. Bob types in his username, bsmith, and his JumpCloud User Account password.
Working with Groups in vCenter
You can set up User Groups to work within vCenter, but because of the Schema issues outlined in User Groups in vCenter above, you cannot import JumpCloud User Groups because of VMware's LDAP Client in the Platform Service Controller.
A successful way to manage Groups with JumpCloud and vCenter is to create Local vsphere.local User Groups and add the JumpCloud LDAP Users to those vsphere.local User Groups. This way, the LDAP Users are membersOf the vsphere.local User Groups and have been given access to the resources in vCenter you've granted them.
Reference our example below:
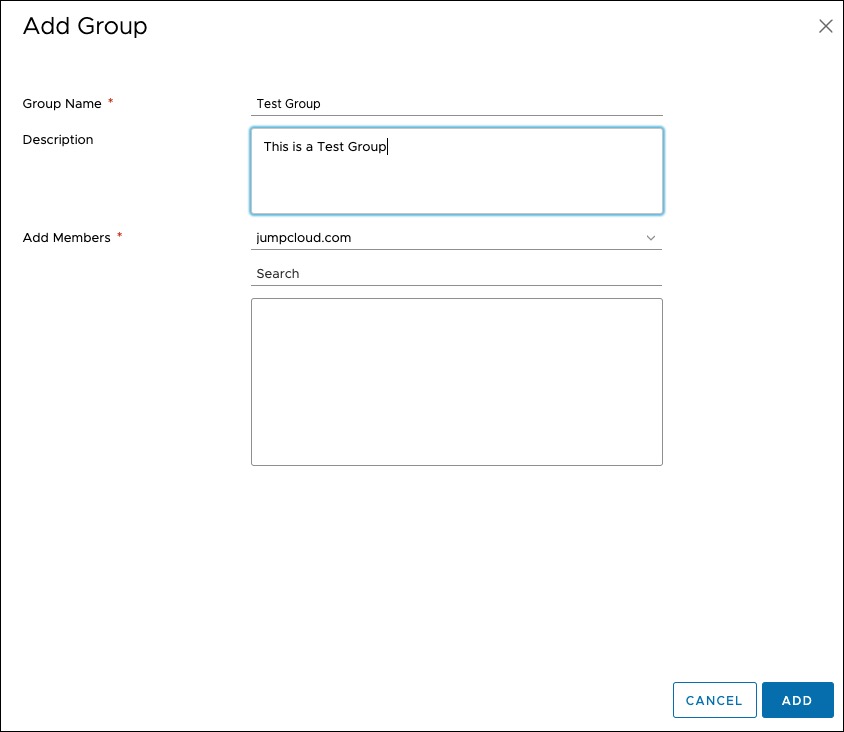
- Adding a group under vCenter's Users and Groups menu, you can create a local vSphere User Group.
- Select a Directory Source. In this case, JumpCloud.com for LDAP users.
- Use the Search field to look up the Users by their JumpCloud Username. Then, add them to the list.
- Once you've added all of your Users to the Group, click Save.
- Add the local vSphere User Group to the objects in the vCenter inventory they need access to and configure their ACLs or Roles within the Inventory list.
JumpCloud LDAP Support and VMware vCenter Support
JumpCloud LDAP is only responsible for the LDAP Authentication of Users to vCenter. JumpCloud LDAP is not responsible for the permissions, ACLs, roles, or any other items that are configured within vCenter or the Platform Service Controller. If users are authenticating to vCenter with their JumpCloud credentials successfully via the method outlined above, then JumpCloud LDAP authentication is working.
vCenter does not support JumpCloud's RFC2307 LDAP Schema in their LDAP client within the Platform Service Controller, and thus cannot import User Groups from JumpCloud into vCenter. This is an issue with VMware's LDAP Client solely supporting Active Directory and RFC4519 in vSphere.
For vCenter permissions issues or other issues within vCenter Server, please reach out to VMware's GSS-SysOps Support Teams.