AWS and JumpCloud have partnered to offer a VPN alternative for securely accessing company applications over the web using JumpCloud Go™, JumpCloud SSO (SAML or OIDC) and AWS Verified Access (AVA). With this collaboration, JumpCloud can authenticate and authorize devices and identities in one console and provide access control for AWS Verified Access for managed devices. See our blog for more information about our partnership.
Prerequisites
- JumpCloud Admin account
- Your JumpCloud Org ID
- JumpCloud SSO Package or higher or SSO add-on feature.
- JumpCloud-managed users on JumpCloud-managed devices
- AWS Admin account (AWS root user)
- AWS organization
There are three steps:
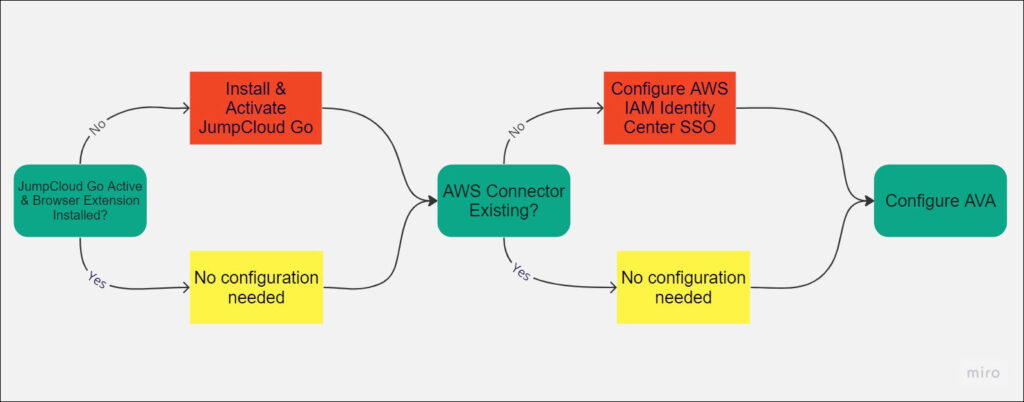
Installing JumpCloud Go
Customers already using JumpCloud Go will have access to AVA with no additional JumpCloud configuration.
The JumpCloud Go Chrome extension provides secure passwordless authentication to JumpCloud protected web resources on managed devices (Mac or Windows). The extension can be installed via JumpCloud Policy, Google’s Chrome Browser Cloud Management (CBCM), or manual installation.
See Get Started: JumpCloud Go and Use JumpCloud Go.
Configuring an AWS SSO Connector
If an AWS IAM Center SSO connector already exists, you can optionally create a second OIDC connector or go to the next section, Setup AVA.
To configure AWS IAM Identity Center SSO
See Integrate with AWS IAM Identity Center.
To configure Custom AWS OIDC
See SSO with OIDC.
For additional information about the AWS OIDC configuration, please view the following AWS documentation:
- AWS Verified Access Integration with 3rd party identity providers
- Using an OpenID Connect trust provider
Setting up AVA
AVA provides secure access to company applications over the internet without using a VPN. Once you have set up JumpCloud Go and the AWS SSO Connector, the final step is configuring Verified Access inside AWS. To proceed, please view the following AWS documentation:
Your JumpCloud Org ID needs to be put in the Tenant ID of AVA.