Integrate JumpCloud and SAP SuccessFactors (SuccessFactors) to unify user identities and centralize user lifecycle management. Users will automatically be created, updated, and suspended in JumpCloud based on their user data in SuccessFactors, saving you time and avoiding mistakes, as well as potential security risks, related to manually creating and updating users Users will be able to access all their work resources with a single user identity. Their access and permissions to resources can automatically change based on updates made in SuccessFactors, ensuring they always have access to the resources they need and nothing else.
Read this article to learn how to setup the SuccessFactors integration using a custom API integration.
Prerequisites
- A JumpCloud administrator account
- JumpCloud SSO Package or higher or SSO add-on feature
- A SuccessFactors administrator account
- Your SuccessFactors domain and company names
- Your SuccessFactors API server name
- The Identity Management integration uses the SuccessFactors SCIM API
- The attributes that are returned from the SAP SuccessFactors SCIM API can be controlled in the SCIM API configuration within the SAP SuccessFactors admin console
- Syncing groups and custom attributes is not supported
Creating a new JumpCloud Application Integration
- Log in to the JumpCloud Admin Portal.
- Go to USER AUTHENTICATION > SSO Applications.
- Click + Add New Application.
- Type the name of the application in the Search field and select it.
- Click Next.
- In the Display Label, type your name for the application. Optionally, you can enter a Description, adjust the User Portal Image and choose to hide or Show in User Portal.
If this is a Bookmark Application, enter your sign-in URL in the Bookmark URL field.
- Optionally, expand Advanced Settings to specify a value for the SSO IdP URL. If no value is entered, it will default to https://sso.jumpcloud.com/saml2/<applicationname>.
The SSO IdP URL is not editable after the application is created. You will have to delete and recreate the connector if you need to edit this field at a later time.
- Click Save Application.
- If successful, click:
- Configure Application and go to the next section
- Close to configure your new application at a later time
Configuring the Identity Management Integration
To configure SuccessFactors
Follow the prerequisites in the Overview of SAP SuccessFactors Workforce System for Cross-Domain Identity Management API article.
Enable the SCIM API user attributes
Control which SCIM user attributes are returned from the SuccessFactors SCIM API. Read Managing Workforce SCIM API Attributes to learn more.
- Log in to SuccessFactors as an admin for your organization.
- Go to Admin Center >Manage Workforce SCIM API Attributes.
- In the User Attributes category, enable the attributes you want returned from the SCIM API. At a minimum, ensure the following attributes are enabled:
- externalId
- locale
- displayName
- nickName
- title
- phoneNumbers
- personIdExternal
- employeeNumber
- emails
- department
- division
- manager
- empId
- Save your changes
First name and last name are returned by default.
Create an account for the integration
- Create an account for the integration.
- Assign Read Users role to the account.
- Set the authorization method to Basic Authentication.
- Securely store the user credentials, like in the JumpCloud Password Manager.
Base64 encode the credentials
- Access the credentials for the integration account.
- Use a tool or commands to base64 encode the credentials:
- Mac - run the following command in the terminal:
base64 <<< <username>@<companyID>:<password> - Windows - run the following command in PowerShell:
$Text = ‘<username>@<companyID>:<password>’
$Bytes = [System.Text.Encoding]::Unicode.GetBytes($Text)
$EncodedText =[Convert]::ToBase64String($Bytes)
$EncodedText
- Mac - run the following command in the terminal:
- Securely store the encoded credentials, like in the JumpCloud Password Manager. This value will be needed when configuring JumpCloud.
To configure JumpCloud
- In JumpCloud, create a new application or select it from the Configured Applications list.
- Select the Identity Management tab.
- Configuration settings > Service Provider Configuration
- API Type - select Custom API
- Authentication method - select API Key
- Base URL - enter https://{api server}/rest/iam/scim/v2
Reference List of SAP SuccessFactors API Servers
- Configuration settings > Service Provider Configuration>Authentication Header
- Header Name - enter Authorization
- Header Value - enter Basic <base64 encoded value>
- Configuration settings > Service Provider Configuration>Authentication Header
- Click + Add Header
- The default Accept header will be added
- Header Value - enter application/scim+json
- Endpoint Configuration > List users > Location:
- Resource Location - Enter Resources
- Method - This field is not changeable and is always set to GET.
- Endpoint Path - enter /Users
- Endpoint Configuration > List users > Total count:
- Response Parameter Location - select body.
- Response Body JSON Path - enter totalResults
- Endpoint Configuration > List users > Pagination:
- Limit Name field - Enter limit
- Offset Name field - Enter skip
- Scroll back up to the top of the Configuration settings section and click Test Connection.
- If successful - you will receive a success message and the fields for attribute mapping will appear
- If unsuccessful - you will receive a failure notification that slides out from the right of the panel and the full error responses received from the service provider will be shown at the bottom of the Configuration Settings section
User Schema Attribute Mapping
Once the connection and credentials have been tested and verified, the user schema mapping section will open. The mappings outlined below are recommended mappings.
- Unique ID - enter id.
- User Status - enter active.
- Inactive Status Values - enter false.
- Complete the two required field mappings by entering the following values in the Service provider attribute JSON path column:
- Company email - enter userName if that has the user's work email. Otherwise, enter emails[0].value
- Username - enter userName if that has the user's work email. Otherwise, enter emails[0].value
- Click Preview to see the SAP employee schema and how the mappings will be applied in JumpCloud.
You can drag the bottom right corner of each section to see the entire schema. You can copy the contents into a text editor to copy and paste attributes.
- Click ok to close the User schema preview window.
- Complete the optional mappings:
- Enter name.givenName for First Name
- Enter name.familyName for Last Name
- Enter title for Job Title
- Enter [urn:ietf:params:scim:schemas:extension:enterprise:2.0:User].department for Department
- Enter [urn:ietf:params:scim:schemas:extension:enterprise:2.0:User].employeeNumber for Employee Identifier
- Enter phoneNumbers[0].value for Work Phone
It is highly recommended to map the attributes marked as suggested, which are the attributes shown in the Optional mappings section by default. The dropdown shows all other user attributes that can be mapped to create a complete user profile.
- Click Preview again to verify the mappings.
- Click ok to close the User schema preview window.
- Click Activate.
Do NOT click Save, you will lose any data you entered in the Identity Management.
- If successful, you will receive a message saying the Identity Management integration has been successfully verified.
- Click save.
Importing Users from SuccessFactors to Jumpcloud
To import with the JumpCloud Admin Portal
- Log in to the JumpCloud Admin Portal.
- Navigate to USER AUTHENTICATION > SSO.
- Search for SuccessFactors and click to open its configuration panel.
- Select the Identity Management tab.
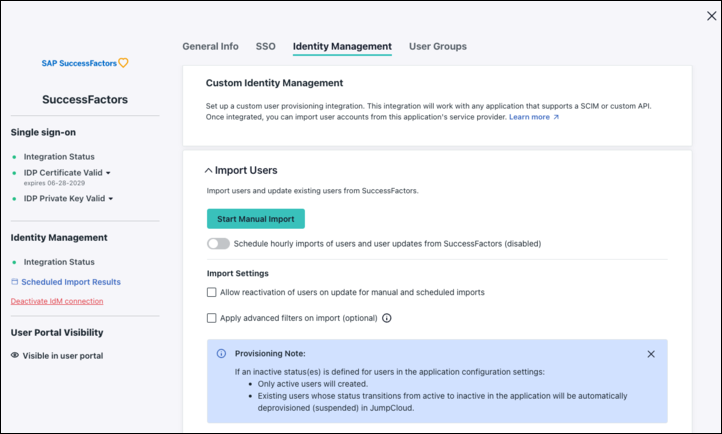
- There are several settings available for importing users from SuccessFactors to JumpCloud.
Selected import options will apply to both manual and scheduled imports.
Import Users
- Manual Import - clicking the Start Manual Import button kicks off the process flow for doing an immediate and one-time import of users from SuccessFactors to JumpCloud.
- Scheduled Imports (hourly) - disabled by default for all new connectors. The first scheduled import will start within an hour after the new connector is saved. Scheduled imports will then run at the same time every hour as the initial scheduled import.
- Selecting the Receive summary email after each scheduled import results in user import complete emails being sent after each hourly import.
It's recommended to enable this for the first few scheduled imports to ensure the imports are running correctly.
Import Settings
- Allow reactivation of users on update - checking the box for this setting will result in the user state changing from Suspended to Active in JumpCloud when a user is terminated in SuccessFactors.
- Apply Advanced Filters on import (optional) - see SuccessFactor's API documentation for available filters.
To limit which users are synced from SAP SuccessFactors to JumpCloud, you can create a group in SAP SuccessFactors named JumpCloud and add a filter for that group to the Import Filter field.
To start a manual import
- Expand the Import Users section and click Start Manual Import.
- Select one of the following options:
- Import new users and user updates
- Only import new users
- Only import user updates
- View and select specific new users to import (updates not supported)
If the option selected includes user updates, the following will occur:
- Any and all changes made to the mapped user attributes in the source application will be made in JumpCloud.
- Users whose statuses change to one of the defined inactive status will be automatically suspended in JumpCloud.
- If Allow reactivation of users on update is checked, suspended users in JumpCloud, whose status change from the defined inactive statuses to ones that are not defined as inactive, will have their user state changed back to Active in JumpCloud.
- Click Continue.
- If you selected the View and select specific new users to import (updates not supported).
- Select the users you want to import.
Trial accounts can import unlimited users, but will be prompted to upgrade to a paid subscription after 30 days. Similarly, accounts managed by an MSP, that have a license limit, are only allowed to import users up to their license limit and will be prompted to contact their provider once that limit is reached.
- The count of users to be imported will show at the bottom left hand of the list. If this is correct, click Import.
- Review the information in the results modal.
- Click one of the tiles to navigate to the Users page, User Groups page, or Device Groups page or close the modal.
If you close this modal, you will return to the Identity Management configuration panel.
- You will receive a User Import Complete email with a summary of the import results and a link for downloading a copy of the import results.
- You can now connect users to all their JumpCloud resources. Learn more in the Authorize Users to an Application and Connecting Users to Resources articles.
Imported users must be members of a user group bound to an application for JumpCloud to manage their identity in and access to the application.
To import users with the JumpCloud API
The import flow using this new API endpoint will only create new users who have an active status in SuccessFactors. See available documentation for this API endpoint.
There are 2 ways to get the application ID for your integration:
- Retrieve the application ID from URL in the JumpCloud Admin Portal:
- Log in to JumpCloud Admin Portal.
- Go to USER AUTHENTICATION > SSO.
- Open the SuccessFactors application by clicking on it.
- Note the ID from the URL which is just before “/details”: https://console.jumpcloud.com/#/sso/{222220da1f777fbe7502cde}/details
- Retrieve the application ID by making a GET /applications request:
curl command example:
curl --request GET \
--url 'https://console.jumpcloud.com/api/applications?fields=id&filter=displayLabel:$eq:SuccessFactors' \
--header 'x-api-key: REPLACE_KEY_VALUE' \
--header 'x-org-id: REPLACE_ORG_ID_VALUE'
- To do a manual import, make a POST /applications/{application_id}/import/jobs request using the application ID from the preceding steps.
curl command example for importing new users and user updates with reactivation of users allowed:
curl --request POST \
--url 'https://console.jumpcloud.com/api/v2/applications/{application_id}/import/jobs' \
--header 'accept: application/json' \
--header 'Content-Type: application/json'\
--header 'x-api-key: REPLACE_KEY_VALUE' \
--header 'x-org-id: REPLACE_ORG_ID_VALUE'\
--data '{
"allowUserReactivation": true,
"operations": [
"users.create",
"users.update"
]
}'
curl command example for importing only user updates:
curl --request POST \
--url 'https://console.jumpcloud.com/api/v2/applications/{application_id}/import/jobs'
--header 'accept: application/json' \
--header 'Content-Type: application/json'\
--header 'x-api-key: REPLACE_KEY_VALUE' \
--header 'x-org-id: REPLACE_ORG_ID_VALUE'\
--data '{
"allowUserReactivation": true,
"operations": [
"users.update"
]
}'
To run scheduled hourly imports
curl command that allows reactivation, sends an advanced import filter, and sends the user import complete email after the hourly sync occurs:
curl --request POST \
--url https://console.jumpcloud.com/api/v2/applications/{applicationObjectId}/import/schedules \
--header 'content-type: application/json' \
--data '{"allowUserReactivation":true,"operations":{"userCreate":true,"userUpdate":true},"query":"string","sendEmail":true}'
Updating the SuccessFactors Identity Management Integration in JumpCloud
- Log in to JumpCloud Admin Portal.
- Go to USER AUTHENTICATION > SSO.
- Search for and select SuccessFactors from the Configured Applications list.
- Select the Identity Management tab.
- Change the desired values
- Click Update.
Configuring the SSO Integration
To configure JumpCloud
- Create a new application or select it from the Configured Applications list.
- Select the SSO tab.
- Replace any instances of YOURDOMAIN and YOURCOMPANY with your SuccessFactors values.
- Add or change any attributes.
- Click save.
Download the JumpCloud metadata file
- Find your application in the Configured Applications list and click anywhere in the row to reopen its configuration window.
- Select the SSO tab and click Export Metadata.
- The JumpCloud-<applicationname>-metadata.xml will be exported to your local Downloads folder.
Metadata can also be downloaded from the Configured Applications list. Search for and select the application in the list and then click Export Metadata in the top right corner of the window.
To configure SuccessFactors
- Contact SuccessFactors' Customer Support and ask them to enable SAML 2.0 Single Sign-On.
- Include the following information with your request:
- Sign-In Page URL - copy the JumpCloud IDP URL
- Sign-Out Page URL - enter https://console.jumpcloud.com/userconsole/
- Attach the metadata file you exported from JumpCloud and send.
Authorizing User SSO Access
Users are implicitly denied access to applications. After you connect an application to JumpCloud, you need to authorize user access to that application. You can authorize user access from the Application Configuration panel or from the Groups Configuration panel.
To authorize user access from the Application Configuration panel
- Log in to the JumpCloud Admin Portal.
- Go to USER AUTHENTICATION > SSO Applications, then select the application to which you want to authorize user access.
- Select the User Groups tab. If you need to create a new group of users, see Get Started: User Groups.
- Select the check box next to the group of users you want to give access.
- Click save.
To learn how to authorize user access from the Groups Configuration panel, see Authorize Users to an SSO Application.
Validating SSO user authentication workflow(s)
IdP-initiated user workflow
- Access the JumpCloud User Console
- Go to Applications and click an application tile to launch it
- JumpCloud asserts the user's identity to the SP and is authenticated without the user having to log in to the application
SP-initiated user workflow
- Go to the SP application login - generally, there is either a special link or an adaptive username field that detects the user is authenticated through SSO
This varies by SP.
- Login redirects the user to JumpCloud where the user enters their JumpCloud credentials
- After the user is logged in successfully, they are redirected back to the SP and automatically logged in
Removing the Integration
These are steps for removing the integration in JumpCloud. Consult your SP's documentation for any additional steps needed to remove the integration in the SP. Failure to remove the integration successfully for both the SP and JumpCloud may result in users losing access to the application.
To deactivate the IdM Integration
- Log in to the JumpCloud Admin Portal.
- Go to USER AUTHENTICATION > SSO Applications.
- Search for the application that you’d like to deactivate and click to open its details panel.
- Under the company name and logo on the left hand panel, click the Deactivate IdM connection link.
- Click confirm.
- If successful, you will receive a confirmation message.
To deactivate the SSO Integration or Bookmark
- Log in to the JumpCloud Admin Portal.
- Go to USER AUTHENTICATION > SSO Applications.
- Search for the application that you’d like to deactivate and click to open its details panel.
- Select the SSO or Bookmark tab.
- Scroll to the bottom of the configuration.
- Click Deactivate SSO or Deactivate Bookmark.
- Click save.
- If successful, you will receive a confirmation message.
To delete the application
- Log in to the JumpCloud Admin Portal.
- Go to USER AUTHENTICATION > SSO Applications.
- Search for the application that you’d like to delete.
- Check the box next to the application to select it.
- Click Delete.
- Enter the number of the applications you are deleting
- Click Delete Application.
- If successful, you will see an application deletion confirmation notification.